|
| 1 | +Terraform module to build east-west security traffic network for Alibaba Cloud |
| 2 | + |
| 3 | +terraform-alicloud-east-west-security-traffic |
| 4 | +====================================== |
| 5 | + |
| 6 | +[English](https://github.com/alibabacloud-automation/terraform-alicloud-east-west-security-traffic/blob/main/README.md) | 简体中文 |
| 7 | + |
| 8 | +在传统数据中心网络中的做法都是部署大量的安全设备组建一个安全域来实现企业系统的安全防护和访问控制,网络流量需要按照业务逻辑和安全防护等级穿过安全域内的不同设备,这就是所谓的服务链(Service Chain)。如今在公共云上部署的实例、容器或微服务之间的互访流量也需要延续相同的安全策略,比如同一个区域的不同VPC之间,VPC和IDC之间等,流量通过安全产品实现基于规则的检测和防护,降低企业内网安全威胁。 |
| 9 | +操作流程简介: |
| 10 | +- 创建业务VPC*2和安全VPC以及配置相关VSW和路由表 |
| 11 | +- 创建云企业网CEN实例以及转发路由器TR |
| 12 | +- 配置TR的VPC连接,并通过TR多路由表实现向安全VPC的引流和回注路由配置 |
| 13 | + |
| 14 | +架构图: |
| 15 | + |
| 16 | +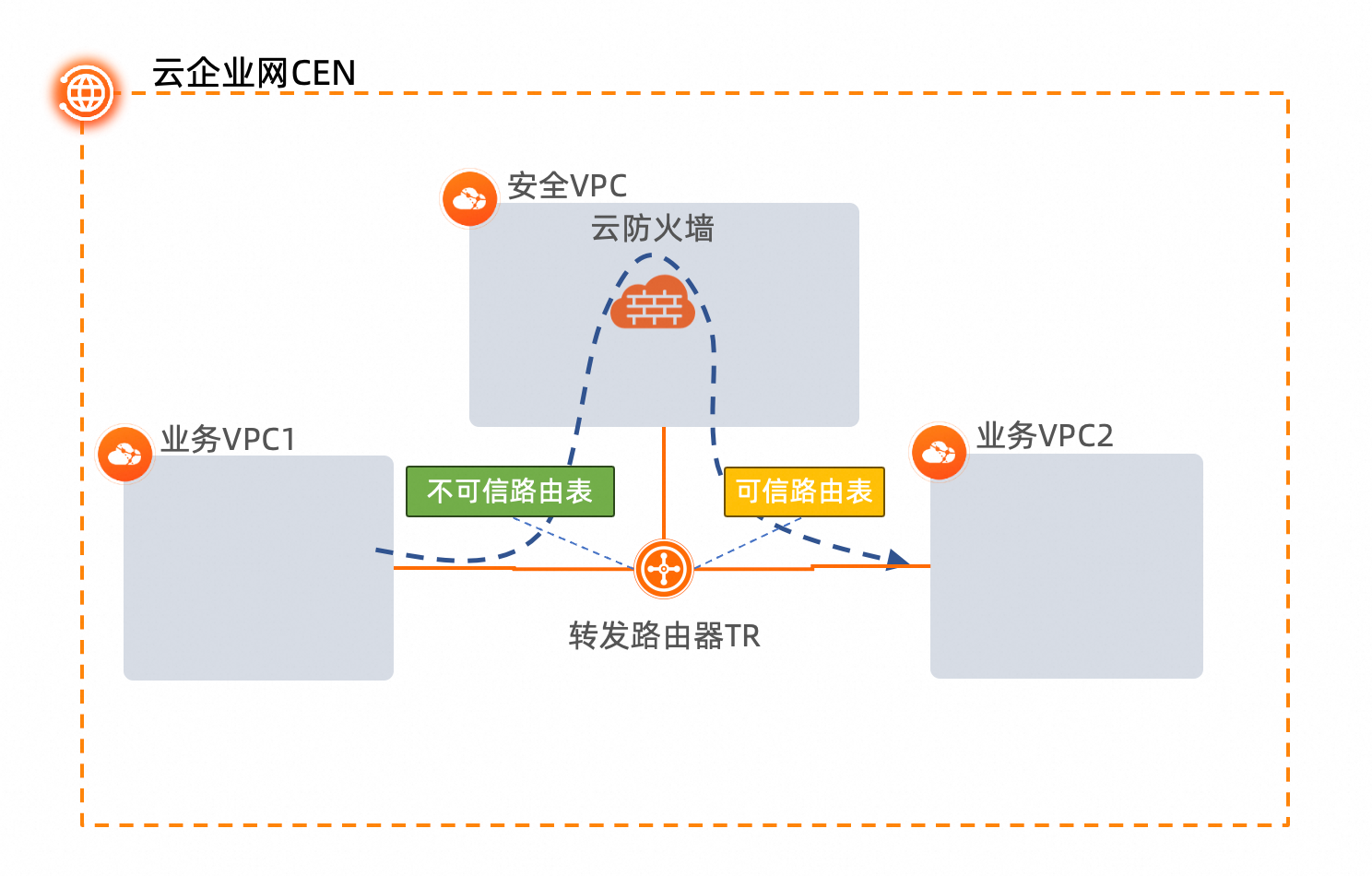 |
| 17 | + |
| 18 | + |
| 19 | +## 用法 |
| 20 | + |
| 21 | + |
| 22 | +```hcl |
| 23 | +provider "alicloud" { |
| 24 | + region = "cn-hangzhou" |
| 25 | +} |
| 26 | +
|
| 27 | +module "complete" { |
| 28 | + source = alibabacloud-automation/east-west-security-traffic/alicloud |
| 29 | +
|
| 30 | + vpcs = [ |
| 31 | + { |
| 32 | + vpc_name = "vpc1", |
| 33 | + cidr_block = "172.16.0.0/24" |
| 34 | + vswitches = [{ |
| 35 | + subnet = "172.16.0.0/25" |
| 36 | + zone_id = "cn-hangzhou-j" |
| 37 | + }, { |
| 38 | + subnet = "172.16.0.128/25" |
| 39 | + zone_id = "cn-hangzhou-k" |
| 40 | + }] |
| 41 | + }, |
| 42 | + { |
| 43 | + vpc_name = "vpc2", |
| 44 | + cidr_block = "192.168.0.0/24" |
| 45 | + vswitches = [{ |
| 46 | + subnet = "192.168.0.0/25" |
| 47 | + zone_id = "cn-hangzhou-j" |
| 48 | + }, { |
| 49 | + subnet = "192.168.0.128/25" |
| 50 | + zone_id = "cn-hangzhou-k" |
| 51 | + }] |
| 52 | + } |
| 53 | + ] |
| 54 | +
|
| 55 | + firewall_vpc = { |
| 56 | + cidr_block = "10.0.0.0/23" |
| 57 | + firewall_vswitch = { |
| 58 | + subnet = "10.0.1.0/24" |
| 59 | + zone_id = "cn-hangzhou-j" |
| 60 | + } |
| 61 | + tr_vswitches = [{ |
| 62 | + subnet = "10.0.0.0/25" |
| 63 | + zone_id = "cn-hangzhou-j" |
| 64 | + }, { |
| 65 | + subnet = "10.0.0.128/25" |
| 66 | + zone_id = "cn-hangzhou-k" |
| 67 | + }] |
| 68 | + } |
| 69 | +} |
| 70 | +``` |
| 71 | + |
| 72 | +## 示例 |
| 73 | + |
| 74 | +* [完整示例](https://github.com/alibabacloud-automation/terraform-alicloud-east-west-security-traffic/tree/main/examples/complete) |
| 75 | + |
| 76 | +<!-- BEGIN_TF_DOCS --> |
| 77 | +## Requirements |
| 78 | + |
| 79 | +| Name | Version | |
| 80 | +|------|---------| |
| 81 | +| <a name="requirement_terraform"></a> [terraform](#requirement\_terraform) | >= 0.13 | |
| 82 | + |
| 83 | +## Providers |
| 84 | + |
| 85 | +| Name | Version | |
| 86 | +|------|---------| |
| 87 | +| <a name="provider_alicloud"></a> [alicloud](#provider\_alicloud) | n/a | |
| 88 | + |
| 89 | +## Modules |
| 90 | + |
| 91 | +| Name | Source | Version | |
| 92 | +|------|--------|---------| |
| 93 | +| <a name="module_vpc"></a> [vpc](#module\_vpc) | ./modules/vpc | n/a | |
| 94 | + |
| 95 | +## Resources |
| 96 | + |
| 97 | +| Name | Type | |
| 98 | +|------|------| |
| 99 | +| [alicloud_cen_instance.this](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_instance) | resource | |
| 100 | +| [alicloud_cen_transit_router.this](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router) | resource | |
| 101 | +| [alicloud_cen_transit_router_route_entry.untrust](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_route_entry) | resource | |
| 102 | +| [alicloud_cen_transit_router_route_table.trust](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_route_table) | resource | |
| 103 | +| [alicloud_cen_transit_router_route_table.untrust](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_route_table) | resource | |
| 104 | +| [alicloud_cen_transit_router_route_table_association.trust](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_route_table_association) | resource | |
| 105 | +| [alicloud_cen_transit_router_route_table_association.untrust](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_route_table_association) | resource | |
| 106 | +| [alicloud_cen_transit_router_route_table_propagation.trust1](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_route_table_propagation) | resource | |
| 107 | +| [alicloud_cen_transit_router_vpc_attachment.firewall_vpc](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/cen_transit_router_vpc_attachment) | resource | |
| 108 | +| [alicloud_route_entry.firewall_vpc_outbound_route](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/route_entry) | resource | |
| 109 | +| [alicloud_route_entry.vpc_default_route](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/route_entry) | resource | |
| 110 | +| [alicloud_route_table.firewall_vpc_inbound_route](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/route_table) | resource | |
| 111 | +| [alicloud_route_table.firewall_vpc_outbound_route](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/route_table) | resource | |
| 112 | +| [alicloud_route_table_attachment.inbound](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/route_table_attachment) | resource | |
| 113 | +| [alicloud_route_table_attachment.outbound](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/route_table_attachment) | resource | |
| 114 | +| [alicloud_vpc.firewall_vpc](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/vpc) | resource | |
| 115 | +| [alicloud_vswitch.firewall_vswitch](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/vswitch) | resource | |
| 116 | +| [alicloud_vswitch.tr_vswitches](https://registry.terraform.io/providers/hashicorp/alicloud/latest/docs/resources/vswitch) | resource | |
| 117 | + |
| 118 | +## Inputs |
| 119 | + |
| 120 | +| Name | Description | Type | Default | Required | |
| 121 | +|------|-------------|------|---------|:--------:| |
| 122 | +| <a name="input_cen_instance_config"></a> [cen\_instance\_config](#input\_cen\_instance\_config) | The parameters of cen instance. | <pre>object({<br> name = optional(string, "east-west-cen")<br> description = optional(string, "east-west-cen")<br> })</pre> | `{}` | no | |
| 123 | +| <a name="input_cen_instance_id"></a> [cen\_instance\_id](#input\_cen\_instance\_id) | The id of an exsiting cen instance. | `string` | `null` | no | |
| 124 | +| <a name="input_cen_transit_router_id"></a> [cen\_transit\_router\_id](#input\_cen\_transit\_router\_id) | The transit router id of an existing transit router. | `string` | `null` | no | |
| 125 | +| <a name="input_create_cen_instance"></a> [create\_cen\_instance](#input\_create\_cen\_instance) | Whether to create cen instance. If false, you can specify an existing cen instance by setting 'cen\_instance\_id'. Default to 'true' | `bool` | `true` | no | |
| 126 | +| <a name="input_create_cen_transit_router"></a> [create\_cen\_transit\_router](#input\_create\_cen\_transit\_router) | Whether to create transit router. If false, you can specify an existing transit router by setting 'cen\_transit\_router\_id'. Default to 'true' | `bool` | `true` | no | |
| 127 | +| <a name="input_firewall_vpc"></a> [firewall\_vpc](#input\_firewall\_vpc) | The parameters of firewall vpc. | <pre>object({<br> vpc_name = optional(string, "firewall-vpc")<br> cidr_block = string<br> firewall_vswitch = object({<br> subnet = string<br> zone_id = string<br> })<br> tr_vswitches = list(object({<br> subnet = string<br> zone_id = string<br> }))<br> inbound_route_table_name = optional(string, "inbound")<br> outbound_route_table_name = optional(string, "outbound")<br> })</pre> | <pre>{<br> "cidr_block": null,<br> "firewall_vswitch": {<br> "subnet": null,<br> "zone_id": null<br> },<br> "tr_vswitches": [<br> {<br> "subnet": null,<br> "zone_id": null<br> },<br> {<br> "subnet": null,<br> "zone_id": null<br> }<br> ]<br>}</pre> | no | |
| 128 | +| <a name="input_tr_config"></a> [tr\_config](#input\_tr\_config) | The parameters of transit router. | <pre>object({<br> name = optional(string, "east-west-tr")<br> untrust_route_table_name = optional(string, "untrust")<br> untrust_route_table_description = optional(string, "untrust")<br> trust_route_table_name = optional(string, "trust")<br> trust_route_table_description = optional(string, "trust")<br> })</pre> | `{}` | no | |
| 129 | +| <a name="input_vpcs"></a> [vpcs](#input\_vpcs) | The parameters of vpc. The attribute 'cidr\_block' is required. | <pre>list(object({<br> vpc_name = optional(string, null)<br> cidr_block = string<br> vswitches = list(object({<br> subnet = string<br> zone_id = string<br> }))<br> }))</pre> | `[]` | no | |
| 130 | + |
| 131 | +## Outputs |
| 132 | + |
| 133 | +| Name | Description | |
| 134 | +|------|-------------| |
| 135 | +| <a name="output_business_tr_vpc_attachment_id"></a> [business\_tr\_vpc\_attachment\_id](#output\_business\_tr\_vpc\_attachment\_id) | The id of attachment between TR and business VPC. | |
| 136 | +| <a name="output_business_vpc_id"></a> [business\_vpc\_id](#output\_business\_vpc\_id) | The ids of business vpc. | |
| 137 | +| <a name="output_business_vpc_route_table_id"></a> [business\_vpc\_route\_table\_id](#output\_business\_vpc\_route\_table\_id) | The route table id of business vpc. | |
| 138 | +| <a name="output_business_vswitch_ids"></a> [business\_vswitch\_ids](#output\_business\_vswitch\_ids) | The ids of business vswitches. | |
| 139 | +| <a name="output_cen_instance_id"></a> [cen\_instance\_id](#output\_cen\_instance\_id) | The id of CEN instance. | |
| 140 | +| <a name="output_cen_transit_router_id"></a> [cen\_transit\_router\_id](#output\_cen\_transit\_router\_id) | The id of CEN transit router. | |
| 141 | +| <a name="output_firewall_tr_vpc_attachment_id"></a> [firewall\_tr\_vpc\_attachment\_id](#output\_firewall\_tr\_vpc\_attachment\_id) | The id of attachment between TR and firewall VPC. | |
| 142 | +| <a name="output_firewall_tr_vswitch_ids"></a> [firewall\_tr\_vswitch\_ids](#output\_firewall\_tr\_vswitch\_ids) | The ids of firewall vswitches. | |
| 143 | +| <a name="output_firewall_vpc_id"></a> [firewall\_vpc\_id](#output\_firewall\_vpc\_id) | The ids of firewall vpc. | |
| 144 | +| <a name="output_firewall_vswitch_id"></a> [firewall\_vswitch\_id](#output\_firewall\_vswitch\_id) | The route table id of firewall vpc. | |
| 145 | +| <a name="output_inbound_route_table_id"></a> [inbound\_route\_table\_id](#output\_inbound\_route\_table\_id) | The id of inbound route table of firewall VPC. | |
| 146 | +| <a name="output_outbound_route_table_id"></a> [outbound\_route\_table\_id](#output\_outbound\_route\_table\_id) | The id of outbound route table of firewall VPC. | |
| 147 | +| <a name="output_trust_route_table_id"></a> [trust\_route\_table\_id](#output\_trust\_route\_table\_id) | The id of trust route table of transit router. | |
| 148 | +| <a name="output_untrust_route_table_id"></a> [untrust\_route\_table\_id](#output\_untrust\_route\_table\_id) | The id of untrust route table of transit router. | |
| 149 | +<!-- END_TF_DOCS --> |
| 150 | + |
| 151 | +## 提交问题 |
| 152 | + |
| 153 | +如果在使用该 Terraform Module 的过程中有任何问题,可以直接创建一个 [Provider Issue](https://github.com/aliyun/terraform-provider-alicloud/issues/new),我们将根据问题描述提供解决方案。 |
| 154 | + |
| 155 | +**注意:** 不建议在该 Module 仓库中直接提交 Issue。 |
| 156 | + |
| 157 | +## 作者 |
| 158 | + |
| 159 | +Created and maintained by Alibaba Cloud Terraform Team(terraform@alibabacloud.com). |
| 160 | + |
| 161 | +## 许可 |
| 162 | + |
| 163 | +MIT Licensed. See LICENSE for full details. |
| 164 | + |
| 165 | +## 参考 |
| 166 | + |
| 167 | +* [Terraform-Provider-Alicloud Github](https://github.com/aliyun/terraform-provider-alicloud) |
| 168 | +* [Terraform-Provider-Alicloud Release](https://releases.hashicorp.com/terraform-provider-alicloud/) |
| 169 | +* [Terraform-Provider-Alicloud Docs](https://registry.terraform.io/providers/aliyun/alicloud/latest/docs) |
0 commit comments